Linux malware is on the rise

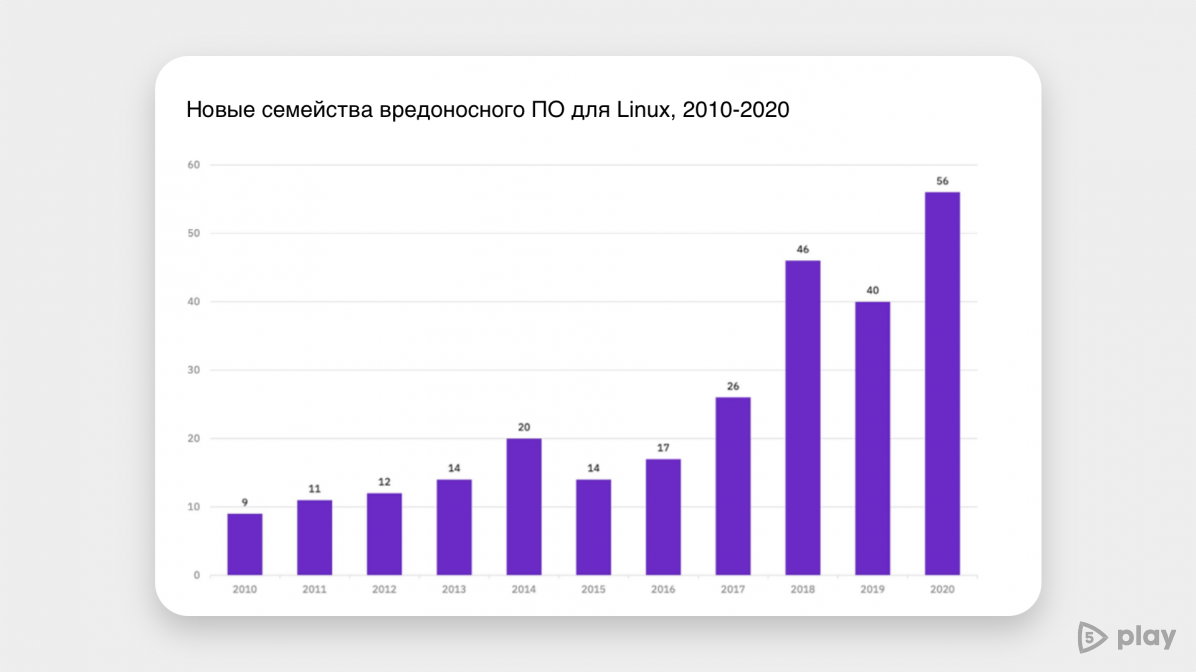
Despite the fact that Linux is one of the most secure systems, the number of virus programs for it is growing every year. Thus, according to a study by CrowdStrike, an information security firm, the volume of such malware has increased by 35% over the past year. In 2020, according to the Intezer portal, the growth was 40%. Then experts found 56 new families of computer viruses.
Three types of malware became the most frequent "guests" of threat telemetry reports. The first is the XorDDoS Trojan, which uses SHH attacks in a brute-force manner; the second is Mirai, used for DDoS attacks; the third is the Mozi botnet, which infects gadgets and mines cryptocurrency with their help.
The increase in indicators is associated with the expansion of the IoT (Internet of Things) market and server equipment. As a rule, devices related to IoT operate on Linux, therefore they are an easy fir tree to hack. In addition, manufacturers of such devices are in no hurry to update software, close outdated ports and set strong passwords. According to Palo Alto Networks, 57% of IoT devices are prone to hacks of medium and high severity.
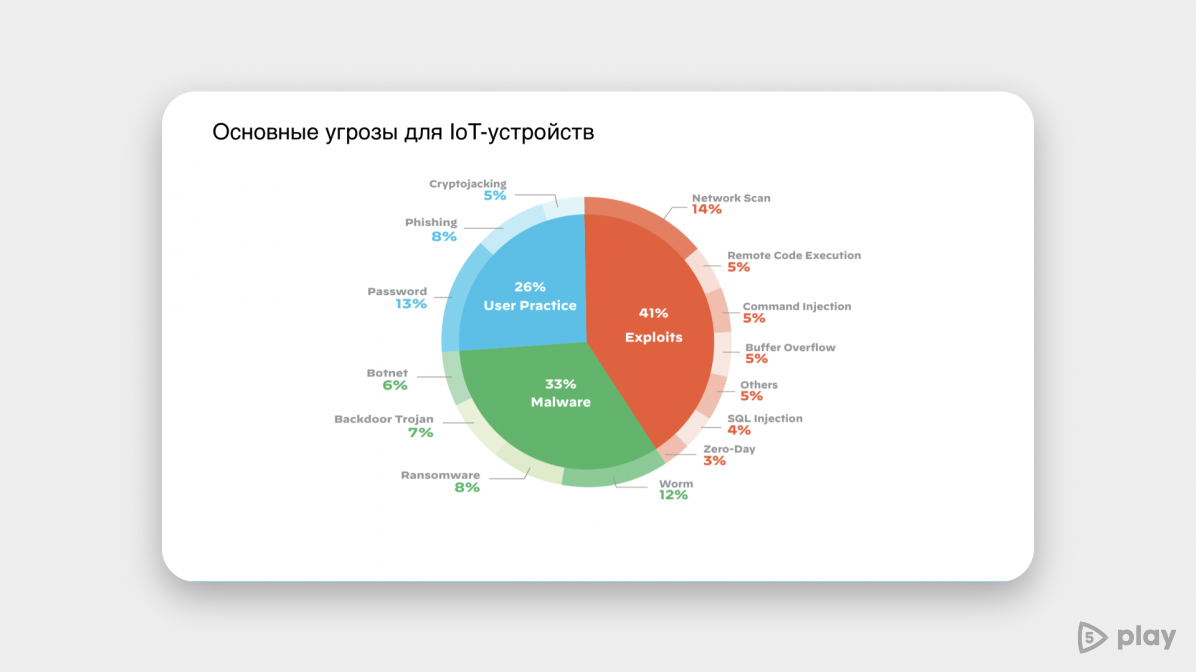
Also, due to the coronavirus pandemic, there is an accelerated introduction of cloud technologies, and 90% of the servers in the cloud operate on Linux. All this attracts the attention of intruders.
The most significant hacker attacks in the previous year
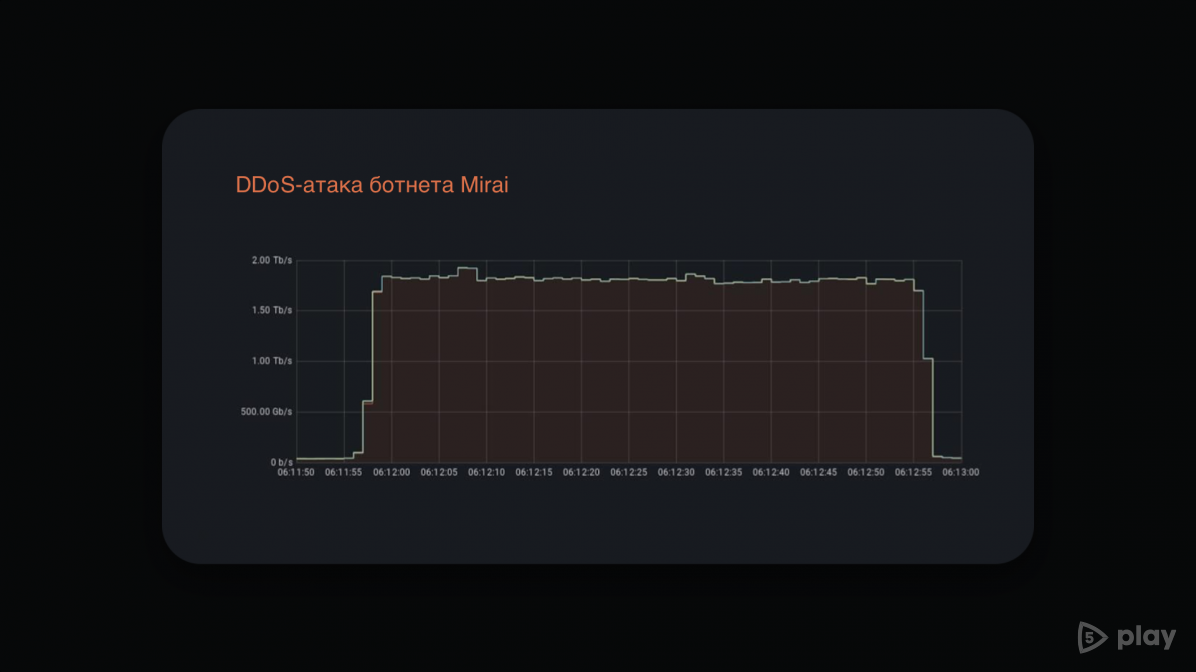
There have been several significant DDoS attacks in 2021. So, in November, Cloudflare was attacked with a capacity of about 2 Tbps. It was produced from 15,000 IoT gadgets, which were combined into the Mirai botnet. In September, Yandex suffered the largest DDoS hack in the history of the Russian-speaking segment of the Internet. Then the attackers used about 56 thousand hacked routers, resulting in a whopping 21.8 million requests per second.
Another popular avenue for cyberattacks has been the use of ransomware. Last summer, the IT company Kaseya suffered at the hands of the hacker group REVill. Damage was caused to about 1,500 client firms of the organization, ranging from shops in Sweden to New Zealand kindergartens. For the restoration of work, REVill wanted to receive a ransom of $ 70 million.
How to protect yourself?
The average user does not have the ability to influence the security of cloud storage, but there is still an opportunity to protect home smart equipment. To do this, you need to consistently update gadget firmware, set complex passwords, use WPA2 and WPA3 technologies to encrypt Wi-Fi networks, and also change devices that are not supported by the vendor.

Three types of malware became the most frequent "guests" of threat telemetry reports. The first is the XorDDoS Trojan, which uses SHH attacks in a brute-force manner; the second is Mirai, used for DDoS attacks; the third is the Mozi botnet, which infects gadgets and mines cryptocurrency with their help.
The increase in indicators is associated with the expansion of the IoT (Internet of Things) market and server equipment. As a rule, devices related to IoT operate on Linux, therefore they are an easy fir tree to hack. In addition, manufacturers of such devices are in no hurry to update software, close outdated ports and set strong passwords. According to Palo Alto Networks, 57% of IoT devices are prone to hacks of medium and high severity.

Also, due to the coronavirus pandemic, there is an accelerated introduction of cloud technologies, and 90% of the servers in the cloud operate on Linux. All this attracts the attention of intruders.
The most significant hacker attacks in the previous year
There have been several significant DDoS attacks in 2021. So, in November, Cloudflare was attacked with a capacity of about 2 Tbps. It was produced from 15,000 IoT gadgets, which were combined into the Mirai botnet. In September, Yandex suffered the largest DDoS hack in the history of the Russian-speaking segment of the Internet. Then the attackers used about 56 thousand hacked routers, resulting in a whopping 21.8 million requests per second.
Another popular avenue for cyberattacks has been the use of ransomware. Last summer, the IT company Kaseya suffered at the hands of the hacker group REVill. Damage was caused to about 1,500 client firms of the organization, ranging from shops in Sweden to New Zealand kindergartens. For the restoration of work, REVill wanted to receive a ransom of $ 70 million.

How to protect yourself?
The average user does not have the ability to influence the security of cloud storage, but there is still an opportunity to protect home smart equipment. To do this, you need to consistently update gadget firmware, set complex passwords, use WPA2 and WPA3 technologies to encrypt Wi-Fi networks, and also change devices that are not supported by the vendor.





There are no comments yet :(